 SECURITY
SECURITY
 SECURITY
SECURITY

 SECURITY
SECURITY
If you come across a security researcher from a company called High Sierra Cyber Security, beware — you may get tricked into downloading malware on your computer.
High Sierra is a cover for a group of hackers who have weaponized social media and the open-source GitHub code repositories. It isn’t the first time this has happened, but it is an interesting case study in how clever these hackers are at worming their way into networks. The scheme was uncovered by cybersecurity researchers VulnCheck Inc. yesterday.
GitHub has been the center of several infamous hacks, such as one last December that had a group of pro-Russian hackers using the site to launch a distributed denial-of-service attack against Ukraine and other European targets. It also has been the site of hackers injecting malware into legit GitHub code repositories, such as the one from last May discovered by Checkmarx Ltd. that affected thousands of GitHub users and projects.
What makes this one noteworthy is two elements.
First, the attack impersonated security researchers, copying images of real analysts and attaching fake names and social media accounts to make them more believable. And like the 2016 election hacks by the Russian Internet Research Agency, each social account referenced other phonies to establish a sense of authenticity and amplify their reach.
This was similar to a 2021 attack that Google’s Threat Analysis Group uncovered. In that attack, the North Korean state-sponsored actors would try to lure legit security researchers into collaborating with them and sending them a malware-infected Microsoft Visual Studio Project source code.
Second, the attack set up a series of GitHub accounts, with each claiming to have zero-day or heretofore undiscovered exploits as lures. The VulnCheck researchers found the original account, which was quickly taken down by GitHub administrators, but new accounts were created and taken down throughout May.
Each account professed to have a different exploit, such as with Signal, WhatsApp, Microsoft Exchange, Google Chrome and Discord. None of these zero-days was legit.
These zero-day exploits are treasured by hackers, because often they can take advantage of backdoors or code misconfigurations, such as what recently was discovered to be the case with Barracuda Networks Inc.’s email gateways. That zero-day vulnerability was patched by the company, although some customers were told to replace their hardware with newer models.
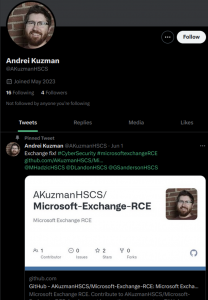 However, instead of a juicy zero-day, the GitHub accounts contained malware in the form of a simple Python script that would download some malicious code. Each GitHub account was tied to a Twitter account that had fake credentials (shown adjacent).
However, instead of a juicy zero-day, the GitHub accounts contained malware in the form of a simple Python script that would download some malicious code. Each GitHub account was tied to a Twitter account that had fake credentials (shown adjacent).
“The attacker has made a lot of effort to create all these fake personas, only to deliver very obvious malware,” the VulnCheck researchers wrote. “It’s unclear if they have been successful, but given that they’ve continued to pursue this avenue of attacks, it seems they believe they will be successful.”
The VulnCheck researchers didn’t claim the origins of the Google 2021 attacks are the same people as the current GitHub attacks, and indeed said the earlier attacks were more sophisticated. The new attacks distributed malware that set off alarms in dozens of antivirus programs, for example.
“It isn’t clear if this is a single individual with too much time on their hands or something more advanced like the campaign uncovered by Google earlier,” they said in their blog post.
THANK YOU